Program of VR NOW Con is updated with awesome sauce!
Our program is online, check out the schedule. We have got news about amazing international speakers (Google, VR Playhouse, LittlStar) and free workshops at the VR NOW Con & Awards in Potsdam and Berlin. Purchase your conference ticket (prices begin at € 199) and get a free MeetToMatch business update.

DOMINIK KÄSER
(Google)
TALK The Making of Google Earth VR, 2pm, Main Stage

In 2014 Dominik started the Google Earth VR project with the goal of letting anyone travel anywhere in virtual reality. Google Earth VR launched in late 2016 to wide acclaim, and went on to win the Lumiere Century award by the Advanced Imaging Society (AIS). It is only the second time in history the AIS handed out a Century Award; the first award went to James Cameron for the movie Avatar.
IAN FORESTER
(VR Playhouse)
TALK Dream Hacking: Subconscious Metrics in the Age of Big Data, 10am, Main Stage

Ian is the CEO and Co-Founder of VR Playhouse and based in Los Angeles. Working in Chicago theater instilled in him a passion for creating transformational experiences. He developed, directed, and performed in dozens of plays and immersive events. After winning LA Weekly’s Award for Best Direction in 2008, he served as the Artistic Director of Needtheater in LA from 2011 until his first encounter with a VR headset in 2014.
LAURA JEFFORDS GREENBERG
(Littlstar)
TALK: A 360 Degree View of Content Performance, 12pm, Alternative Stage

Laura is the Senior VP of Business & Legal Affairs at Littlstar, the leading global platform dedicated to immersive virtual reality and 360° content. She manages and oversees the company’s legal department, advising the company on international content acquisitionand distribution, development and licensing of software and applications, and business operations. Before that she was Senior Legal Counsel at Red Bull Media House in Austria.
ALL SPEAKERS SO FAR
Gabo Arora (Lightshed), Melek Balgün (Moderator), Thomas Bedenk (Exozet), Sven Bliedung (Slice Studios), AC Coppens (The Marketing Catalyst), Kristian Costa-Zahn (Ufa Lab), Maria Courtial (FaberCourtial), Daan Kip (VRBase), Susanne Dickel (IntoVR), Sebastian Endler (Amilux FIlmproduktion), Ian Forester (VR Playhouse), Pawel Gajda (Carbon Studio), Christian Glessner (Hololux), Laura Jeffords Greenberg (LittlStar), Peter Hu (Auctoreal), Ioulia Isserlis (AnotherWorld VR), Dominik Käser (Google), Sönke Kirchhof (INVR), Marcus Kühne (Audi), Gerda Leopold (Amilux Filmproduktion), Pieter van Leugenhagen (Yondr), Rebecca Liu (VRCORE), Pedro Lopes (Hasso-Plattner-Institut), Greg Louden (3rd Eye Studios), Yiming Niu (VRARA China Chapter), Gayatri Parameswaran (NowHere Media), Lina Reinsbakken (Norn Studio), Max Sacker (AnotherWorld VR), Max Salomon (Blackdotfilms), Dr. Oliver Schreer (Fraunhofer Institut), Christopher Sibley (Phenomenon Media), Daniel Sproll (realities.io), Sara Lisa Vogl (VRBAse), Sven Slazenger (Interlake) Andrew Van Wyk (River Road Entertainment) – and many more.
Helping Hands for Ca$h

You are interested in VR, AR, MR, and other forms of enhanced realities? You want to discover new trends and thoughts? Want to get insights in the industry and meet the makers and shakers of the future of VR? You are just curious and know you will make a good contribution to the event? Great! Fill out this form and we will come back to you!
Please note: some jobs are paid, so its best you have a valid VAT number in Germany (not mandatory!). You get a small fee, a free tickets, catering and we make sure your work is also fun!
Please fill out this form to be part of the movement!
https://docs.google.com/forms/d/e/1FAIpQLSeqMq97MyMyXtuo9eGrZzhOwAnhQhhD7ZujiL0BICxsW4u7yw/viewform
Intel Buzz Workshop Poznan – how to make it in South America
We’re ready to go. Check out our speakers Intel Buzz Workshop at October 7 during the GIC in Poznan.

The Latin American market for video games is more different to the Western market than one thinks. With different platforms (last generation consoles are still very popular in the three biggest markets Brazil, Mexico and Argentina), business models, paying modalities and so on.
André Faure is CEO of GamePlan, one of the main business influencers in the Latin Americas. André has launched over 100 products including software, hardware, media and services.
His talk is called and will be about “Games in Latin America – Market, Trends, Tips and Tricks” (2.30-3 pm).
Intel Buzz Workshop Poznan –Valentina Tamer & the Pillars of Earth
We’re ready to go. Check out our speakers Intel Buzz Workshop at October 7 during the GIC in Poznan.

Carving a video game out of an existing franchise – is it easier or more difficult than creating everything from the scratch? How do you handle creative freedom and demands of the IP owners? And how do you turn a book into a video game?
Valentina Tamer is working for Hamburg based developer/publisher Daedalic Entertainment. Her current project: the world famous Pillars of Earth which was originally written by Ken Follett.
The Point’n Click adaption is already well received. In her talk (3-3.30 pm), Valentina explains the work on quest and story design.
Intel Buzz Workshop Poznan – Stefan Ljungqvist, maker of Biomutant
We’re ready to go. Check out our speakers Intel Buzz Workshop at October 7 during the GIC in Poznan.

Stefan Ljungqvist, Head of Studio at Experiment 101. Maker of Biomutant. Breaker of Chains. Writer of children’s literature. He actually wrote books that were translated and sold in seven countries. His latest is called Monsterflickan 5 – Återföreningen, which can be translated with Monster Girl 5 – The Reunion.

Responsible for studio strategy, creative direction and product development at Experiment 101. His talk (10.15-11 am) is about balancing creativity and management for Biomutant, the recently announced and already awaited Action-RPG.
Intel Buzz Workshop Poznan – play DOOM with John Romero
We’re ready to go. Check out our speakers Intel Buzz Workshop at October 7 during the GIC in Poznan.
Yes, he’s coming. John Romero, father of DOOM and Quake and the whole flipping FPS genre. In a fireside chat with Michael Liebe (11.30-12.30) he’ll be talking about the good ole’ times when he got to ID Software, about level design and creativity management. Also: get the chance to play DOOM with him.

Game Jam – Use Case No.3: Unraveling the anonymity paradox!

Unveil the Privacy Threat – that’s how we named the Game Jam (October 7, 2017) we’re going to host together with the Alexander von Humboldt Institute for Internet and Society – will be fun and serious. And we want you to be part of it.
We will present to you three different use cases with a direct connection to data security and privacy by design. We have invited prominent experts to talk about the importance of data privacy, advise and inspire the participants of the Game Jam. What are the use cases, who are the experts? This is use case No 3.
Use case 3: Unraveling the anonymity paradox!

What sounds like the title of a 60′s psycho thriller B-Movie for mathematicians is in fact a modern day horror story. Here’s why.
If personal information were anonymized, all our privacy concerns would be gone! But what does “anonymized” mean?
This question is one of the hardest to resolve in the privacy debate. At present, privacy experts are grappling with the paradox that – in the big data era – there is no anonymous data anymore.
All data can always be related to an individual by means of data analysis technologies. The reason for this is that data is only considered “anonymized” if it cannot be related to an identified or even to an identifiable individual.
In order to understand this paradox, imagine this:
More than three million Berlin citizens – and another million tourists – are carrying around their personal devices every single day. There’s a Berlin-wide wifi system, which is publicly available for all people who have switched on their devices’ wifi by default. This wifi system collects the movement data of all these devices over a longer period of time.
Guess how useful this data would be for urban traffic management and many other innovations. But wouldn’t it be creepy if this data could also be misused against an individual later on?
This data is thus anonymized in order to mitigate these risks. In the process all personal identifiers (i.e. the MAC address and IMEI) of the devices captured by the wifi system – which could in principle lead to an identification of the owner or even carrier of a device – are “hashed” (i.e. substituted by a specific hash value for each identifier).
This hash value does not per se contain information referring to the owner or carrier of the device. However, it is still possible to capture the device’s movement pattern by referring to this hash. This movement pattern becomes more and more precise over time.
A person who gets access to that movement pattern (e.g. an employee of the provider of the wifi system or another data-driven company) might suddenly discover that this device must be owned by somebody he knows very well.
The reason for this is that this device “leaves” the building where he lives at the same time every morning and “moves” to an address where only lawyers work: In terms of probability, that person must be his wife!
This risk of re-identification of “anonymized” data exists generally, where it is combined with further information.
It is hard to say which information will be added and hard to say what the consequences of an identification are. It is hard to say under which conditions this risk is low enough in order to be socially acceptable.
Assignment
The goal of this use case is to develop an engaging game concept that helps people to understand the anonymity paradox. One target group are people working in companies specifically dealing with anonymized data (e.g. such as the provider of the wifi system described).
Want to join the Unveil the Privacy Threat Game Jam on October 7, 2017 in Berlin? Register here for free.
The best game idea will be awarded by an expert jury with an exciting prize – a weekend trip to London for the whole winning team including a visit of The Crystal, the world’s largest museum on the future of (smart) cities – sponsored by Siemens. Furthermore, amongst all participants, we give away two one-year-memberships of Adobe Creative Cloud sponsored by Adobe.*
*without possibility of recourse to legal action
Text by Max von Grafenstein
Game Jam – Use Case No.2: Oops… wrong recipient ?
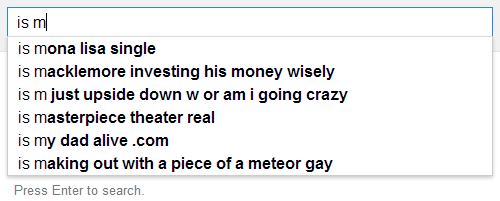
Unveil the Privacy Threat – that’s how we named the Game Jam (October 7, 2017) we’re going to host together with the Alexander von Humboldt Institute for Internet and Society. It will be fun and serious. And we want you to be part of it.
We will present to you three different use cases with a direct connection to data security and privacy by design. We have invited prominent experts to talk about the importance of data privacy, advise and inspire the participants of the Game Jam. What are the use cases, who are the experts? This is use case No 2.
Use Case 2: Oops… wrong recipient ?
The most common privacy threat in companies arises when an employee accidentally sends personal information about somebody else to the wrong recipient.
This may sound like a no-brainer, but in fact, it is one of the biggest challenges in implementing effective privacy protection policies within companies.
There are two typical constellations that give rise to slightly different challenges for companies trying to mitigate this threat:
In the first constellation, an employee uses an email client, and in the second constellation, he/she grants access to a file depository.
In both cases, an employee typically sends an email or grants access to a repository to the wrong recipient – because the email client or repository incorrectly autocompletes the address based on the first few letters.
The employee forgets to double-check the name and… oops, the information is sent to the wrong recipient.
But there are differences between the cases: They refer to how such an employee can react. If the employee has granted access to a file repository, in principle, he or she can still restrict access retrospectively.

In contrast, if the employee has sent an email, the information is definitely “gone”, and he or she can only ask the recipient not to read and/or open the content.
However, in both cases employees often do not react at all, or they do not appropriately, because they fear negative consequences if his or her colleagues or superior find out about it.
Assignment
The goal of this use case is to develop an engaging game concept that reduces the privacy threat as a result of sending personal information to the wrong recipient, in a playful manner. One target group of such a game are employees in companies dealing with personal data in general.
Want to join the Unveil the Privacy Threat Game Jam on October 7, 2017 in Berlin? Register here for free.
The best game idea will be awarded by an expert jury with an exciting prize – a weekend trip to London for the whole winning team including a visit of The Crystal, the world’s largest museum on the future of (smart) cities – sponsored by Siemens. Furthermore, amongst all participants, we give away two one-year-memberships of Adobe Creative Cloud sponsored by Adobe.*
*without possibility of recourse to legal action
Text by Max von Grafenstein










