Intel Buzz Workshop Poznan – play DOOM with John Romero
We’re ready to go. Check out our speakers Intel Buzz Workshop at October 7 during the GIC in Poznan.
Yes, he’s coming. John Romero, father of DOOM and Quake and the whole flipping FPS genre. In a fireside chat with Michael Liebe (11.30-12.30) he’ll be talking about the good ole’ times when he got to ID Software, about level design and creativity management. Also: get the chance to play DOOM with him.

Game Jam – Use Case No.3: Unraveling the anonymity paradox!

Unveil the Privacy Threat – that’s how we named the Game Jam (October 7, 2017) we’re going to host together with the Alexander von Humboldt Institute for Internet and Society – will be fun and serious. And we want you to be part of it.
We will present to you three different use cases with a direct connection to data security and privacy by design. We have invited prominent experts to talk about the importance of data privacy, advise and inspire the participants of the Game Jam. What are the use cases, who are the experts? This is use case No 3.
Use case 3: Unraveling the anonymity paradox!

What sounds like the title of a 60′s psycho thriller B-Movie for mathematicians is in fact a modern day horror story. Here’s why.
If personal information were anonymized, all our privacy concerns would be gone! But what does “anonymized” mean?
This question is one of the hardest to resolve in the privacy debate. At present, privacy experts are grappling with the paradox that – in the big data era – there is no anonymous data anymore.
All data can always be related to an individual by means of data analysis technologies. The reason for this is that data is only considered “anonymized” if it cannot be related to an identified or even to an identifiable individual.
In order to understand this paradox, imagine this:
More than three million Berlin citizens – and another million tourists – are carrying around their personal devices every single day. There’s a Berlin-wide wifi system, which is publicly available for all people who have switched on their devices’ wifi by default. This wifi system collects the movement data of all these devices over a longer period of time.
Guess how useful this data would be for urban traffic management and many other innovations. But wouldn’t it be creepy if this data could also be misused against an individual later on?
This data is thus anonymized in order to mitigate these risks. In the process all personal identifiers (i.e. the MAC address and IMEI) of the devices captured by the wifi system – which could in principle lead to an identification of the owner or even carrier of a device – are “hashed” (i.e. substituted by a specific hash value for each identifier).
This hash value does not per se contain information referring to the owner or carrier of the device. However, it is still possible to capture the device’s movement pattern by referring to this hash. This movement pattern becomes more and more precise over time.
A person who gets access to that movement pattern (e.g. an employee of the provider of the wifi system or another data-driven company) might suddenly discover that this device must be owned by somebody he knows very well.
The reason for this is that this device “leaves” the building where he lives at the same time every morning and “moves” to an address where only lawyers work: In terms of probability, that person must be his wife!
This risk of re-identification of “anonymized” data exists generally, where it is combined with further information.
It is hard to say which information will be added and hard to say what the consequences of an identification are. It is hard to say under which conditions this risk is low enough in order to be socially acceptable.
Assignment
The goal of this use case is to develop an engaging game concept that helps people to understand the anonymity paradox. One target group are people working in companies specifically dealing with anonymized data (e.g. such as the provider of the wifi system described).
Want to join the Unveil the Privacy Threat Game Jam on October 7, 2017 in Berlin? Register here for free.
The best game idea will be awarded by an expert jury with an exciting prize – a weekend trip to London for the whole winning team including a visit of The Crystal, the world’s largest museum on the future of (smart) cities – sponsored by Siemens. Furthermore, amongst all participants, we give away two one-year-memberships of Adobe Creative Cloud sponsored by Adobe.*
*without possibility of recourse to legal action
Text by Max von Grafenstein
Game Jam – Use Case No.2: Oops… wrong recipient ?
Unveil the Privacy Threat – that’s how we named the Game Jam (October 7, 2017) we’re going to host together with the Alexander von Humboldt Institute for Internet and Society. It will be fun and serious. And we want you to be part of it.
We will present to you three different use cases with a direct connection to data security and privacy by design. We have invited prominent experts to talk about the importance of data privacy, advise and inspire the participants of the Game Jam. What are the use cases, who are the experts? This is use case No 2.
Use Case 2: Oops… wrong recipient ?
The most common privacy threat in companies arises when an employee accidentally sends personal information about somebody else to the wrong recipient.
This may sound like a no-brainer, but in fact, it is one of the biggest challenges in implementing effective privacy protection policies within companies.
There are two typical constellations that give rise to slightly different challenges for companies trying to mitigate this threat:
In the first constellation, an employee uses an email client, and in the second constellation, he/she grants access to a file depository.
In both cases, an employee typically sends an email or grants access to a repository to the wrong recipient – because the email client or repository incorrectly autocompletes the address based on the first few letters.
The employee forgets to double-check the name and… oops, the information is sent to the wrong recipient.
But there are differences between the cases: They refer to how such an employee can react. If the employee has granted access to a file repository, in principle, he or she can still restrict access retrospectively.

In contrast, if the employee has sent an email, the information is definitely “gone”, and he or she can only ask the recipient not to read and/or open the content.
However, in both cases employees often do not react at all, or they do not appropriately, because they fear negative consequences if his or her colleagues or superior find out about it.
Assignment
The goal of this use case is to develop an engaging game concept that reduces the privacy threat as a result of sending personal information to the wrong recipient, in a playful manner. One target group of such a game are employees in companies dealing with personal data in general.
Want to join the Unveil the Privacy Threat Game Jam on October 7, 2017 in Berlin? Register here for free.
The best game idea will be awarded by an expert jury with an exciting prize – a weekend trip to London for the whole winning team including a visit of The Crystal, the world’s largest museum on the future of (smart) cities – sponsored by Siemens. Furthermore, amongst all participants, we give away two one-year-memberships of Adobe Creative Cloud sponsored by Adobe.*
*without possibility of recourse to legal action
Text by Max von Grafenstein
Register to win a 1-year-membership of Adobe’s Creative Cloud

Maybe you’ve heard about it: We’re hosting a Game Jam with a dedicated topic. Unveil the Privacy Threat covers data privacy and privacy by design. We’re still looking for participants. And we’re giving away a 1-year-membership for Adobe’s Creative Cloud. The whole package, including stock photos and all the useful tools for digital creatives. How?
We will draw the winner of the Adobe Creative Cloud membership among every sincere registration for the Game Jam Unveil the Privacy Threat.*
What you have to do? Simply follow THIS LINK and fill out the registration form on the website of the Alexander von Humboldt Institute for Internet and Society (HIIG).
The institute is our partner and came up with the idea of hosting this Game Jam in the first place.
Find out more about the details of the package worth more than 1000 Euros HERE.
Again we would like to thank Adobe for the uncomplicated provision of this generous price.
*without possibility of recourse to legal action
Game Jam – Use Case No.1: I’ve got nothing to hide!

Unveil the Privacy Threat – that’s how we named the Game Jam (October 7, 2017) we’re going to host together with the Alexander von Humboldt Institute for Internet and Society – will be fun and serious. And we want you to be part of it.
We will present to you three different use cases with a direct connection to data security and privacy by design. We have invited prominent experts to talk about the importance of data privacy, advise and inspire the participants of the Game Jam. What are the use cases, who are the experts? This is use case No 1.
Use Case 1: I’ve got nothing to hide!
Many people think they’ve got nothing to hide and thus do not need to protect their privacy. The reasoning behind this is that only people who have done something illegal would want to conceal their behavior. But, so the thinking goes, there’s no social need for protection for illegal behavior! Or is there?
This only relates to a tiny part of privacy protection. In fact, privacy laws doesn’t just protect those (allegedly) engaged in “illegal” behavior. Privacy also protects a person against the loss of reputation that can occur when information is disclosed and/or used in the wrong context.
As early as the 17th century, the French high priest and statesman Cardinal Richelieu stated:
“Give me a letter of six sentences written by the most honorable man, and I will find something sufficient to hang him.”

Henri Motte’s depiction of Cardinal Richelieu at the Siege of La Rochelle.
At least in Germany we don’t hang people anymore. However, what this kind of reasoning indicates is that there can always be somebody who wants to use personal information against someone. It’s this misuse of personal information that privacy seeks to protect against.
Some people even say that it actually doesn’t matter what you may have to hide; what matters is your ability to decide whether to hide something or not. This ability is guaranteed by privacy.
Privacy is hence an essential precondition for the enrollment of an autonomous personality.
Assignment
The goal of this use case is to develop an engaging game concept that challenges the “nothing-to-hide” argument in a playful manner. Ideally, such a game could be played anywhere, at any time, in a very limited period of time. Just like a quick-fire schoolyard debate.
A Wikipedia article for basic information about the Nothing to Hide argument.
An EFF guide to how to respond to the Nothing to Hide argument.
One of many useful YouTube videos about this topic.
Want to join the Unveil the Privacy Threat Game Jam on October 7, 2017 in Berlin? Register here for free.The best game idea will be awarded by an expert jury with an exciting prize – a weekend trip to London for the whole winning team including a visit of The Crystal, the world’s largest museum on the future of (smart) cities – sponsored by Siemens.
Furthermore, amongst all participants, we give away two one-year-memberships of Adobe Creative Cloud sponsored by Adobe.*
*without possibility of recourse to legal action
Text by Max von Grafenstein
Booster Space at the Asian New Media Film Festival

Our Program Director Tim was in China. Instead of inviting you to a slideshow and bore you with 657 unselected snapshots, we only post a few.
Tim at the Asian New Media Film Festival in Shenzhen, China. Tim speaking with other experts on a panel about storytelling in VR in short pants because British Airways has indefinitely lost his baggage (though he still believes he gets compensated fairly). Tim in front of his signature, proud as a peacock at the award ceremony in Macao. Tim with fancy sunglasses in front of the HTC ViveX HQ. And a stereotypical aerial view with a fancy blue hipster photo filter. This was an important step to curate the program of the VR NOW Con & Awards. Mark your calendar: 15-16 November.






VR NOW Con & Awards – Submit Your Project

Give us your best shot. Submit your hyper immersive VR experience. Your thrilling 360 degree movie. Your VR game masterpiece. Your convincing business model for VR, AR and every digital enhanced reality you can imagine.
The VR NOW Con Awards 2017 celebrate outstanding technical, business, and artistic achievements in Virtual Reality. They are part of the VR NOW Conference, taking place in Potsdam/Berlin on November 15-16, 2017.
You can submit your project and compete against an international community of friends and strangers, fellow creatives, beautiful minds and smart business cats.
Where do I submit?
Please note that applying for the VR NOW Con Awards and paying the application fee on this page doesn’t give you access to the award show. Only VR NOW Con ticket holders will be allowed to participate in the award show.
Yet, a successful application gives you a discount of 25 % (that’s nearly one third) on the ticket price.
Please use the discount link you get with your confirmation of submission.NOMINEES GET A FREE EXHIBITION SPACE DURING THE EVENT on Nov 15+16, 2017.
What’s in for me?
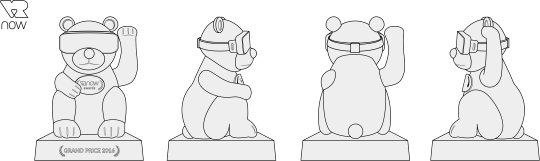
This animal. It’s called Winkebär.

It’s a hybrid version of the Maneki-neko…

… and the heraldic animal of Berlin, the Berliner Bär (photo by Ebert).
It’s also our trophy.
With each submission, contestants receive a VR NOW Con ticket discount code of 25%. The discount code will be sent via email once the submission has been approved.
Each of the nominees will receive 2 VR NOW Con business tickets (worth 499,- euros each), a dedicated space in the nominees exhibition area to present their project during the event and a mention in the pre-event press release.
Each of the award winners will receive a trophy, a 1-year Virtual Reality e.V. Berlin-Brandenburg association membership, a mention in the post-event press release and will be featured in the newsletter of our funding partner Medienboard Berlin-Brandenburg, in addition to the honor that goes with winning the second VR NOW Con Award.
Do you have dedicated award categories?
Yes. Even with a new formula! Four projects will be nominated for each of the following categories:
VR NOW Grand Prize
The best virtual reality project of the year, based on overall quality and innovation. The best of the best of the best.
VR Tech Award
The VR Technology Award seeks to recognize the technically most advanced Virtual Reality projects, tools, services, hardware and techniques.
VR Entertainment Award
The VR Entertainment Award acknowledges the most outstanding and fun experience – including interactive, storydriven or experimental formats.
VR Industry Award
The VR Industry Award highlights handy and innovative virtual reality business-to-business applications and solutions.
VR Impact Award
With the VR Impact Award we support projects aimed at making a difference – through journalism, artistic expression or by social or non-profit organizations.
Can I submit my immersive high school project from 1993?
Nope. Any virtual reality project is eligible as long as it has been first exhibited or released to the public between December 2016 and September 2017. Sorry, no ancient vomiting machines allowed.
Submissions must be compatible with one of the following platforms: Gear VR, Google Cardboard, HTC Vive (consumer version), Oculus Rift (consumer version), PlayStation VR, Microsof Hololens. Projects not compatible with any of these platforms can still be submitted, as long as the applicant provides the jury an opportunity to evaluate them in Berlin, Germany.
How much of my money do you want for that?
Not much. We aren’t going to fill our pockets with of your hard earned $€¥. Actually, our fees are quiet fair.
Early Bird fee: 25 € + 19% tax (ends August 6, 2017)
Regular fee: 40 € + 19% tax (ends October 1, 2017)
Please note that applying for the VR NOW Con Awards and paying the application fee on this page doesn’t give you access to the award show. Only VR NOW Con ticket holders will be allowed to participate to the award show.
Everybody is a goldmine –A Game Jam to implement privacy and security by design

If we want tech to be more human, we’ll need to create awareness about privacy in the age of smart cities and IoT. That’s why we’re going to host a Game Jam about this subject, together with the Humboldt Institute for Internet and Society and INNOVATION & LAW. And you can apply.
Private data is the number one resource of our time. It’s what gold and oil have been in the past centuries. Our user behavior – including the tiniest subconscious decisions we make when we use smart devices and browser interfaces – is a fine but steady load that’s been mined for many years now.
To stick with this simple analogy: right now heavy machinery is invented to drill deeper. Thanks to the IoT the monitored behavior isn’t reduced to hardware we use deliberately.
The whole city will become a computer. Sensors are going to be everywhere in the smart cities of the near future. And with great data comes great responsibility.
We have to ask ourselves how we want to handle data protection and privacy in a society that seems to be dependent on progress by information.
How can we establish awareness, not only among political activists and digital rights experts but people who engineer software, plan parking lots or open networks for the public benefit?
For our partners Alexander von Humboldt Institute for Internet and Society and INNOVATION AND LAW, we’re going to host a Game Jam.
The outcome we’re hoping for? Interactive and fun approaches on why data privacy and security is something we have to think of while developing a service or product.
This awareness will have two effects: Privacy by design or privacy by default will become a standard for on the one side – and more trust in tech and progress on the other side.
GAME JAM – UNVEIL THE PRIVACY THREAD Implementing privacy and security through games
will take place on the weekend of 7-8 October at the premises of the Alexander von Humboldt Institute for Internet and Society in Berlin. There’ll be impulse talks by experts for inspiration and knowledge extension.
Right now you can apply by simply writing an email to hi@booster-space.com. Please explain in two, three sentences why you apply / how you want to contribute.


